In the last article available here http://tombrett.ie/ransomware-part-1-what-is-ransomware/ we looked at what ransomware is, this current article takes a brief look at the history of ransomware from its earliest forms to 1989 to some current attacks. The next article will look at variants of ransomware and then shouls we pay or not and methods to mitigate the risk of becoming infected.
Held for Ransom – it all began in the middle ages!
The practice of ransom dates back to the middle ages, where initially it was the amount of money paid for the successful the capture of a knight. The capture of these knights where they were worth a significant amount of money if brought back alive, this amount was then commonly used to measure a knight’s heraldry.
Due to the fact that the ransom meant that knights would be captured alive, the Knights would commonly let their identity be known as it minimised the possibility of them being killed in an attack due to the ransom.
Ransom – the Digital Space
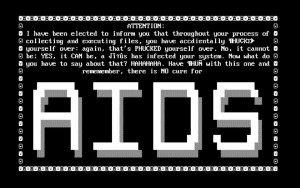
The earliest documented instance of ransomware in the digital space was in 1989. This was with the introduction of the PC Cyborg Trojan (more commonly known as the AIDS Trojan) which was sent via floppy diskettes to attendees at the World Health Organization’s international AIDS conference.
This Trojan hid directories and encrypted the names of files. In order for users to gain access to their data, they had to send $189 dollars to a PO Box in Panama, belonging to PC Cyborg Corp. The attacker, Dr Joseph L Popp mysteriously enough was never prosecuted as his attorney declared him unfit for trial due to the fact that he had been wearing a cardboard box on his head to protect him from radiation! (Knowbe4.com, 2016) Joseph was therefore declared medically unfit to go to trial but seemingly promised to pay the profits to Aids research.
A screenshot of the message recipients received is illustrated below.
A weakness with the Cyborg Trojan ransomware was that it used symmetric encryption (Same key), in a paper entitled ‘Cryptovirology: Extortion-Based Security Threats and Countermeasures’ released in 1996 by two researchers Adam Young and Moti Yung identified these weaknesses and explaining how to use public-key cryptography in ransomware, making reverse-engineering virtually impossible. (Young & Yung, 1996)
Other than this unusually early form in 1989, the next cases were in Russia between 2005 and 2006 were a couple of cases in Russia around 2005. These variants created password protected zip files and deleted the original file, they also created text files with the ransom notes within.
A while later, CryptoLocker surfaced in September 2013, targeting all versions of Windows, distributed via emails impersonating customer support services from FedEx, UPS, DHS and other companies demanding average payments of 300 dollars in 72 hours. (Kaspersky.com, 2016)
Little did the writers noted earlier (Young and Yung) know the effect that their research and paper which includes the use of public key encryption where they “defne a cryptographic attack to be a denial of service attack using a public key. The attack is survivable unless the virus writer reverses it.” (Young & Yung, 1996) This can definitely be seen as the turning point where ransomware manufacturers would use asymmetric key encryption to increase their rate of success of being paid due to the fact that the key would not be reused nor stored locally.
References
Balakrishnan, A. (2016). The hospital held hostage by hackers. Retrieved March 15, 2016, from http://www.cnbc.com/2016/02/16/the-hospital-held-hostage-by-hackers.html
Bitcoin.org. (2016). Bitcoin. Retrieved from https://bitcoin.org/en/
Bray, H. (2015). Tewksbury police pay bitcoin ransom to hackers – The Boston Globe. Retrieved March 22, 2016, from https://www.bostonglobe.com/business/2015/04/06/tewksbury-police-pay-bitcoin-ransom-hackers/PkcE1GBTOfU52p31F9FM5L/story.html
FBI.gov. (2015). FBI — Ransomware on the Rise. Retrieved March 14, 2016, from https://www.fbi.gov/news/stories/2015/january/ransomware-on-the-rise
Ferguson, M. (2015). Why was Ransomware So Successful in Australia? ~ Security, So What? Retrieved March 16, 2016, from http://www.securitysowhat.com/2015/04/why-was-ransomware-so-succcess-in.html
Finkle, J. (2016). Mac ransomware caught before large number of computers infected | Reuters. Retrieved March 15, 2016, from http://www.reuters.com/article/us-apple-ransomware-idUSKCN0W80VX
Kaspersky.com. (2016). What is Ransomware? | Prevention & Removal | Kaspersky Lab US. Retrieved March 14, 2016, from https://usa.kaspersky.com/internet-security-center/definitions/what-is-ransomware
Kirk, J. (2014). “Reveton” ransomware upgraded with powerful password stealer | PCWorld. Retrieved March 14, 2016, from http://www.pcworld.com/article/2466980/reveton-ransomware-upgraded-with-powerful-password-stealer.html
Kleczynski, M. (2016). Introducing the Malwarebytes Anti-Ransomware Beta | Malwarebytes Labs. Retrieved March 16, 2016, from https://blog.malwarebytes.org/news/2016/01/introducing-the-malwarebytes-anti-ransomware-beta/
Knowbe4.com. (2016). AIDS Trojan or PC Cyborg Ransomware. Retrieved March 14, 2016, from https://www.knowbe4.com/aids-trojan
Kroustek, J. (2016). Ransomware on the rise – how to protect your devices and data. Retrieved March 14, 2016, from http://now.avg.com/ransomware-on-the-rise-how-to-protect-your-devices-and-data/
Lincolnshire County Council hit by £1m malware demand – BBC News. (2016). Retrieved February 1, 2016, from http://www.bbc.com/news/uk-england-lincolnshire-35443434
McAfee Labs. (2015). Meet “Tox”: Ransomware for the Rest of Us – McAfee. Retrieved March 15, 2016, from https://blogs.mcafee.com/mcafee-labs/meet-tox-ransomware-for-the-rest-of-us/
Metzger, M. (2016). Canadian hospital infected with ransomware – SC Magazine UK. Retrieved March 22, 2016, from http://www.scmagazineuk.com/canadian-hospital-infected-with-ransomware/article/484003/
Millman, R. (2016). Ransomware holds data hostage in two German hospitals – SC Magazine UK. Retrieved March 15, 2016, from http://www.scmagazineuk.com/ransomware-holds-data-hostage-in-two-german-hospitals/article/479683/
Mogg, T. (2016). Hollywood hospital pays $17,000 to ransomware hackers | Digital Trends. Retrieved March 15, 2016, from http://www.digitaltrends.com/computing/hollywood-hospital-ransomware-attack/
Nakashima, E., & Zapotosky, M. (2016). These hackers can hold a town hostage. And they want ransom — paid in bitcoin. – The Washington Post. Retrieved March 22, 2016, from https://www.washingtonpost.com/world/national-security/these-hackers-can-hold-a-town-hostage-and-they-want-ransom–paid-in-bitcoin/2016/03/18/1a2e2494-eba9-11e5-bc08-3e03a5b41910_story.html
O’Regan, M. (2016). Hackers demand €20k as firms hit by “ransomware” – Independent.ie. Retrieved March 15, 2016, from http://www.independent.ie/irish-news/hackers-demand-20k-as-firms-hit-by-ransomware-34515040.html
Peters, S. (2015). Police Pay Off Ransomware Operators, Again. Retrieved March 14, 2016, from http://www.darkreading.com/attacks-breaches/police-pay-off-ransomware-operators-again/d/d-id/1319918
Steffen, S. (2016). Hackers hold German hospital data hostage | Germany | DW.COM | 25.02.2016. Retrieved March 15, 2016, from http://www.dw.com/en/hackers-hold-german-hospital-data-hostage/a-19076030
Us-Cert.gov. (2014). Crypto Ransomware | US-CERT. Retrieved March 16, 2016, from https://www.us-cert.gov/ncas/alerts/TA14-295A
Weckler, A. (2016). Stand and deliver – the ransomware wave ravaging Irish SMEs – Independent.ie. Retrieved March 16, 2016, from http://www.independent.ie/business/technology/stand-and-deliver-the-ransomware-wave-ravaging-irish-smes-34526253.html
Young, A., & Yung, M. (1996). Cryptovirology: Extortion Based Security Threats and Countermeasures. Retrieved March 22, 2016, from http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.121.3120&rep=rep1&type=pdf
Zinopy.ie. (2016). Irish Government hit by new wave of ransomware attacks – Zinopy. Retrieved March 15, 2016, from http://www.zinopy.ie/news/irish-government-hit-new-wave-ransomware-attacks/