This is part 1 of a multipart series!
In this article we will look at what Ransomware is, where it originated and the increasing risks accordingly, this article will be followed up with subsequent articles looking at different forms of ransomware and targeted devices, how ransomware work and methods to minimise the risk prevent the need to pay the ransom demands to recover your data.
You are working on large project remotely, all of your files are on your laptop and due to the location you have not backed it up for a few weeks. You turn on your laptop to continue where you left off only to discover that you have been locked out of all of your files…..
A ransom note appears, explaining that you have a week to pay the equivalent of 500 euros in Bitcoins or the price will go up each and every day until you pay. You therefore have the option of paying up or losing all of your data! The message has been written in bad English, you have no other way to get access to your work, but you are also unsure that if you do pay – can you trust them, will you ever get access?
What are you going to do, weeks of work has been locked up away from access. You decide to do some investigation of your own, you access another machine and do some online searches, it seems that this is an ever growing threat, there are loads of cases both large and small organisations as well as Government bodies and even police forces which have been hit with similar attacks and to make it worse, there does not seem to be a silver bullet, some police departments have paid attackers between 300 and 500 dollars in Bitcoins for the recovery of encrypted files (Peters, 2015).
You have just become another victim of ransomware, don’t take it personally though as most ransomware attacks are not actually targeted, you may have just stumbled onto a compromised website.
What is Ransomware
Ransomware is a form of malware, which prevents you from accessing your files until you pay an amount of money demanded by the attacker known as a ransom, this ransom is generally paid via Bitcoins which is an open source public payment method offering a high level of anonymity (Bitcoin.org, 2016).
Several versions of ransomware have been released over the years with more recent variants getting more advanced not only targeting windows workstations like earlier versions but now also targeting apple devices, tablet’s and mobile phones.
Most forms of ransomware do not corrupt the operating system but prevent access to the data files, some by merely preventing access others by encrypting the actual files, as well as encrypting the files on the device itself, they will also encrypt the data on any interconnected storage shares and devices causing havoc in the enterprise due to this data loss and/or downtime whilst backups are being restored.
There are two general types of ransomware:
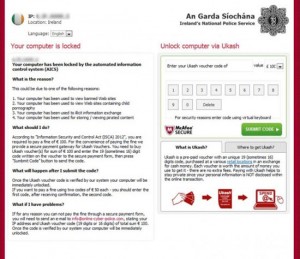
- Locker Ransomware: commonly referred to as ‘Computer locker’, this form merely denies access to the computer or device, this does not meant that the content is encrypted or corrupted in any way. In a lot of cases, locker ransomware restricts access to the data via the OS with full screen applications wrote and designed to prevent access (see figure 1) showing a payment voucher entry area where
proof of payment could be submitted to close the application and allow access again. To resolve some of these cases, a mere system restore or the removal registry entries or files from the start-up via safe mode allowed users to regain access to their data.
- Crypto ransomware: commonly referred to as ‘Data locker’, this variant actually prevents access to the user’s data files. It does not necessarily have to use encryption to prevent users from accessing data, but most do!
Earlier forms of Crypto ransomware used symmetric encryption, storing the key within the registry allowing users with enough knowledge to gain access to the key and then use this to decrypt the data, later versions use asymmetric key cryptography, generating keys on the fly specific to the individual systems, storing the keys in the cloud on their server and wiping the local key from memory. Thus preventing the user from having any access to the keys, therefore having no means of decrypting the data without paying the ransom demanded.
Infection
Ransomware can infect devices via a number of methods, it is commonly downloaded by unsuspecting users from visiting compromised or malicious websites, but it can also arrive as a payload, downloaded as a file from a website or an attachment via email. Because of this, ransomware is generally not targeted, but in some cases certain types of websites may be created or infected which may then target certain groups of users.
In the next part of this multipart series, I will look at the brief history of ransomware from its early days of the PS Cyborg Trojan to the current Ransomware as a Service (Tox) variants and most forms in between, after this I will then look at methods which we can use to minimise the risk of infection.
References
Balakrishnan, A. (2016). The hospital held hostage by hackers. Retrieved March 15, 2016, from http://www.cnbc.com/2016/02/16/the-hospital-held-hostage-by-hackers.html
Bitcoin.org. (2016). Bitcoin. Retrieved from https://bitcoin.org/en/
blogs.mcafee.com. (2015). Meet “Tox”: Ransomware for the Rest of Us – McAfee. Retrieved March 15, 2016, from https://blogs.mcafee.com/mcafee-labs/meet-tox-ransomware-for-the-rest-of-us/
FBI.gov. (2015). FBI — Ransomware on the Rise. Retrieved March 14, 2016, from https://www.fbi.gov/news/stories/2015/january/ransomware-on-the-rise
Finkle, J. (2016). Mac ransomware caught before large number of computers infected | Reuters. Retrieved March 15, 2016, from http://www.reuters.com/article/us-apple-ransomware-idUSKCN0W80VX
Kirk, J. (2014). “Reveton” ransomware upgraded with powerful password stealer | PCWorld. Retrieved March 14, 2016, from http://www.pcworld.com/article/2466980/reveton-ransomware-upgraded-with-powerful-password-stealer.html
Knowbe4.com. (n.d.). AIDS Trojan or PC Cyborg Ransomware. Retrieved March 14, 2016, from https://www.knowbe4.com/aids-trojan
Kroustek, J. (2016). Ransomware on the rise – how to protect your devices and data. Retrieved March 14, 2016, from http://now.avg.com/ransomware-on-the-rise-how-to-protect-your-devices-and-data/
Labs, K. (n.d.). What is Ransomware? | Prevention & Removal | Kaspersky Lab US. Retrieved March 14, 2016, from https://usa.kaspersky.com/internet-security-center/definitions/what-is-ransomware
Lincolnshire County Council hit by £1m malware demand – BBC News. (2016). Retrieved February 1, 2016, from http://www.bbc.com/news/uk-england-lincolnshire-35443434
Millman, R. (2016). Ransomware holds data hostage in two German hospitals – SC Magazine UK. Retrieved March 15, 2016, from http://www.scmagazineuk.com/ransomware-holds-data-hostage-in-two-german-hospitals/article/479683/
Mogg, T. (2016). Hollywood hospital pays $17,000 to ransomware hackers | Digital Trends. Retrieved March 15, 2016, from http://www.digitaltrends.com/computing/hollywood-hospital-ransomware-attack/
O’Regan, M. (2016). Hackers demand €20k as firms hit by “ransomware” – Independent.ie. Retrieved March 15, 2016, from http://www.independent.ie/irish-news/hackers-demand-20k-as-firms-hit-by-ransomware-34515040.html
Peters, S. (2015). Police Pay Off Ransomware Operators, Again. Retrieved March 14, 2016, from http://www.darkreading.com/attacks-breaches/police-pay-off-ransomware-operators-again/d/d-id/1319918
Steffen, S. (2016). Hackers hold German hospital data hostage | Germany | DW.COM | 25.02.2016. Retrieved March 15, 2016, from http://www.dw.com/en/hackers-hold-german-hospital-data-hostage/a-19076030
Zinopy.ie. (2016). Irish Government hit by new wave of ransomware attacks – Zinopy. Retrieved March 15, 2016, from http://www.zinopy.ie/news/irish-government-hit-new-wave-ransomware-attacks/