What are passwords used for?
Passwords are combined usually with usernames to validate (authenticate) that a user is who they claim to be, although other forms (factors) of authentication exist passwords are the most common used method, this is generally due to their ease of use from both user and administrator point of view and their setup requires no special equipment or procedures.
Factors of Authentication
Factors of authentication are the different types of methods which can be used to authenticate (prove that the user is who they say that they are)
There are three general factors of authentication
- Authentication by Knowledge (What you know – Passwords etc.)
- Authentication by Characteristic (who you are – Biometrics, fingerprints etc.)
- Authentication by Ownership (What you have – Key cards etc.)
Strong Authentication
Strong Authentication, also known as multi-factor authentication is the use of two or more of the different factors of authentication.
A good easy to understand example of multi-factor authentication is a bank Card, you need to have the card (something you have – Ownership) along with the PIN code (Something you know – Knowledge)
With all of these different factors of authentication available including multi-factor authentication, the question which many ask is: should we still use passwords, are they secure?
Are Passwords Secure
Michael Chertoff (former head of Homeland Security) stated in a report on CNBC.com that “A closer examination of major breaches reveals a common theme: In every ‘major headline’ breach, the attack vector has been the common password. The reason is simple: The password is by far the weakest link in cybersecurity today.”(Chertoff, 2016) In this report Michael further states that “we need to acknowledge the failure of passwords and make it a national priority to come up with something better – leveraging the next generation of authentication technologies to authenticate identities in a way that is both stronger than passwords and also easier for people to use.”
The biggest concern has to be the fact that we have known that weak passwords have been the cause of a number of security incidents for years and yet we have not learnt, we still see and use weak passwords.
Trustwave.com published a report in 2012 outlining areas of vulnerabilities persisting within organisations, for this report they studied more than 300 data breaches in the year 2011 across 18 countries.
Most of this report was devoted to weak password protection where eighty percent of the incidents were due to the use of weak or default credentials. This report highlighted an instance where an attacker was able to compromise 250 unique systems in a single target by exploiting duplicate credentials!(Trustwave.com, 2012).
The Most Common Passwords of 2016
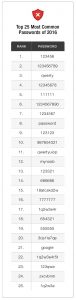
According to a study conducted by KeeperSecurity.com using 10 million passwords from data breaches in 2016 the most common password being used (almost 17% of the group studied) was “123456” with the second most common being “123456789”! The report also confirmed the other expected suspects “password”, “qwerty” and so on, please see figure below for the full list. (Guccione, 2017)
An even more frightening analysis is that users are not learning, in 2012 Trustwave.com reported that “123456” which is now the most common password, was previously the seventh most common password used in 2012 (Trustwave.com, 2012).This same password was also found in a password dump file back in 2010 used in two hundred and fifty thousand accounts!. The report stated that “the Gawker Media network, which includes popular websites such as Lifehacker, Gizmodo, Jezebel, io9, Jalopnik, Kotaku, Deadspin, Fleshbot, and of course Gawker, was compromised yesterday. The hacker group Gnosis posted a torrent containing a full dump of Gawker’s source code as well as the entire user database consisting of 1.3 million usernames, email addresses, and DES-based crypt password hashes.”(Duo Labs, 2010)
Amongst the list of most commonly used passwords were some complex variants, but the report highlighted that “Security expert Graham Cluley believes that the presence of seemingly random passwords such as ‘18atcskd2w’ and ‘3rjs1la7qe’ on the list indicates that bots use these codes over and over when they set up dummy accounts on public email services for spam and phishing attacks.”
Another interesting point noted in the study include the fact that “four of the top 10 passwords on the list – and seven of the top 15 – are six characters or shorter” This proved that a number of providers are still not enforcing password lengths let alone complexity and that users are still not attempting to secure their own passwords.
Figure 1: 25 most common passwords of 2016. Source https://blog.keepersecurity.com/2017/01/13/most-common-passwords-of-2016-research-study/
Another problem with the use of these common passwords is in the name, that they are ‘common’, they are previously known and therefore expected passwords, it is quiet common that when sites are hacked that the users account details including their passwords are made available online, A report published by Duo.com back in 2010 highlighted the Gawker Media network attack and the dumping of account passwords online.(Duo Labs, 2010)
Good Password ingredients
In order for passwords to be secure they must:
- Be Complex, Long and impossible to guess!
- they must keep them secure,
- they must be constantly changed!
Here we will look in turn at each of the three ingredients which allow us to secure a password.
Complex, Long and Impossible to guess
As we have illustrated earlier, it is far too easy to create a password which is easy to remember or guess and that passwords using common words, phrases or patterns like “qwerty” and “12345” are all too easy to guess. What about other terms or words.
In order to identify the most ‘Secure Types’ of passwords, one has to look at the methods used to crack a password.
Three core versions of password cracking exist, Dictionary, Brute Force attacks and Rainbow Tables.
Each of these involve the use of applications which automate the process of cracking passwords, these together with faster hardware enables hackers to crack passwords faster than ever before.
Brute Force Attacks
With a Brute Force attack the attacker will use a piece of software or script to use every combination of character (or the characters picked) against the password. The hacker will identify the approximate length of the password (usually by a min and max length) the software will then use every combination of character in every arrangement until it has exhausted the variants or cracked the password. Due to the possible amount of combinations this may take months or even years, so brute force attacks are normally done on smaller passwords, as if passwords are being changed regularly the password will have changed prior to the password being found!
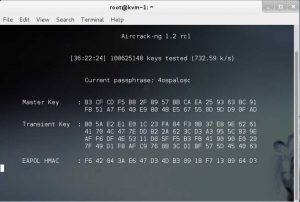
Below is a screenshot of Aircrack-ng which is currently doing a Brute Force attack and running 36+ hours but generating and processing 732.59 password keys per second (please note that with higher end machines and specific graphics cards, this number can be massively increased!) The current passphrase “4ospalosc” can be seen which was generated and tried at the time of the screen capture.
Figure 2: Aircrack-ng
Dictionary Attacks
In a Dictionary attack, dictionary files are used which literally contain thousands of words and common phrases which are then used alongside a password cracking script or program to ‘try’ each variant against the password until the list is exhausted or the password has been identified.
Dictionary files can be created using different languages, they can even be purchased online containing passwords which have been used in compromised sites allowing hackers access to previously used passwords and phrases.
Dictionary Attacks can also be supplemented with Character Substitution where the attacker identifies the characters with the dictionary to also be tried with user changed characters, this will allow the attacker to instruct the program or script to substitute ‘S’ with commonly used characters like ‘$’ or ‘5’ increasing the likeness of success!
Rainbow Tables
Passwords are generally (and recommended) stored using a one-way encryption known as a hash or digest whereby the user enters a password in plain text, this goes through an algorithm which encrypts the password and stores the output. When the user logs in, they re-enter the plaintext version, the software again hashes it and compares it against the recorded hash. If the hashes are identical authentication is successful, if they are different user access is denied.
Rainbow tables are generated collections of hashes and their plaintext equivalent which allows the hacker to compare the hashed versions against the stored password hash and identify the plaintext used. The use of Rainbow Tables allow for passwords to be cracked in a very short amount of time compared to brute-force attacks, the trade-off is that it takes a lot of storage to hold the Rainbow Tables themselves. Hackers can purchase Rainbow table files for this use, some of these come from hacked websites where the hashing algorithm has been identified.
So what defines a Secure Password?
If there can be such a thing as a secure password, or even a password less prone to being hacked what are the main components?
Length or Complexity?
A common question is whether passwords should be longer and less complex or shorter and more complex, usually people choose short complex, but are short complex passwords more secure than longer ones? The simple answer here is no, in fact longer passwords with no complexity can be considered stronger than short complex ones (as long as it is not a dictionary term!). This is due to entropy. Entropy is simply the total number of states that something can be in, so with regards to passwords, larger character sets combined with more characters create stronger passwords.
In an online article by StormPath.com the Author Brent talks about the myth of Complex passwords being more secure than long passwords, he states that “People often think of a short set of random characters like ‘*K>#)0$j4’ as super secure, but a long string of memorable words like ‘golfkangaroocrispyhalitosis’ is actually stronger”. Brent further states that “The reason has everything to do with password entropy: a representation of how much uncertainty there is in a password. This translates to how computationally difficult a password is to crack. Simply put, adding length increases entropy more efficiently than replacing letters with symbols.”(Jensen, 2013)
What is the desired length then?
Although most systems require approximately 8 characters, the minimum password length should be between 10 and 14 characters. In the NIST special publication 800-132 they specify that passwords shorter than 10 characters are considered weak.(Turan et al., 2010) Passwords should also not be limited to the 8 or 16 characters which some sites and applications define.
Just remember that each character which you add, makes your password harder to crack based on entropy.
Password Character set
The password character set is the type of characters used in the formation of the password. Passwords should contain non normal characters (‘$’, ‘_’, ‘+’, ‘%’, ‘^’, ‘&’ etc.) and not be limited to Alpha (letters) or Alpha Numerical Characters (letters and numbers).
Also don’t forget that when using Character Substitution, not to choose common Substituted characters like ‘@’ for ‘a’, ‘$’ for s etc. as hackers will know and will build these into the attacking program, instead create your own unique character substitution set! (but remember, keep it secret).
Keeping Passwords Secure
When we have created that ‘secure’ password, we need to be careful where we use it. We need to ensure that it does not fall into the wrong hands. This can happen with social engineering and Pharming sites (Pharming sites are when a user is redirected to a fake site in order to harvest your credentials. This is stressed by Michael Chertoff, when he stated that “even when so-called ‘strong’ passwords are required, they are still vulnerable to phishing attacks, key-loggers and other compromises”.(Chertoff, 2016)
We also should not record them somewhere that they can be found! There are a number of common locations where users record passwords, these include Diaries, Calendars, the common ‘Post-it note’ and even the more secure Password Management Site, browser or application.
Each and every one of these can be vulnerable. Even the Password manager, which has additional risks because if an attacker gains access to that they have ‘the keys to the kingdom!’ Password Managers also get hacked and are known to have had vulnerabilities which may be exploited, in a previous article I wrote about LastPass and its vulnerability which was found by Tavis Ormandy allowing anyone to proxy unauthenticated messages to the LastPass browser extension. (Brett, 2017)
We should use different passwords for each site due to the fact that if one site gets hacked it may be used to compromise other sites which you use the same credentials (especially your email account).
Constantly changing Passwords
There is definitely evidence which proves that changing passwords more frequently does not necessarily create more secure accounts due to users choosing passwords which are easier to remember. In a study conducted in 2010, researchers at the University of North Carolina looked at a data set consisting of thousands of old passwords belonging to former university students, faculty and staff who had to change their password every three months. This study found that users followed patterns that linked old passwords to new passwords, these patterns included methods like swapping the order of meaningful numbers and letters, replacing a letter with a common number or symbol substitute, or adding or removing special characters like exclamation marks.
The researchers in the study created a too which allowed them to predict how users would change passwords, which worked for 41 percent of accounts in less than three seconds at that time and allowed them to determine passwords for 17 percent of the accounts in fewer than five guesses. (Zhang, Monrose, & Reiter, 2010)
Does this mean that we should not change our passwords, No it definitely does not!
As we have identified earlier, even complex passwords can be cracked with brute force and dictionary attacks given enough time. Also the more we use a password puts it at more risk, simply put the more we enter a password the more the potential for it to be exposed to a phishing site, keylogger or even a site that gets hacked. If any of these happen with our password, the attacker has access to the accounts until such time as you change it.
What about Multiple Accounts?
If we think back to authentication in general, it requires two pieces of information, one is the username which is commonly your email address the second is your password. I have always advocated the use of at least two email accounts, what I would consider a fluffy or non-secure account and then the more secure account. Your non-secure account should not identify you in any way (not use your real name) and it should only be used when you wish to register for informational sites and not anything secure, this then protects your main account somewhat from being harvested. Because you never use the fluffy or non-secure account for anything important and private, if it ever gets hacked it is not a major problem, it is important that the two account functions do not cross though. Your secure account then is used for just that, secure logins.
So what does this all mean?
Yes it is true, if used incorrectly the use of passwords may make a system insecure, but if used correctly, they can still be used to create a secure authentication system. The answer though is to educate users in the correct generation and use of passwords and to identify the risks or improper use.
I have been involved in a number of Security / Cyber Awareness briefings and seminars over the years and find that once staff understand the risks that they become more responsible with the generation and use of passwords in their everyday life
References
Brett, T. (2017). With the recent LastPass Vulnerability – Should we use Password Managers at all? – TomBrett.ie. Retrieved April 13, 2017, from http://tombrett.ie/recent-lastpass-vulnerability-use-password-managers/
Chertoff, M. (2016). Passwords are the weakest link in cybersecurity today—Michael Chertoff—commentary. Retrieved April 13, 2017, from http://www.cnbc.com/2016/10/06/passwords-are-the-weakest-link-in-cybersecurity-today-michael-chertoff-commentary.html
Duo Labs. (2010). Brief Analysis of the Gawker Password Dump | Duo Security. Retrieved April 13, 2017, from https://duo.com/blog/brief-analysis-of-the-gawker-password-dump
Guccione, D. (2017). What the Most Common Passwords of 2016 List Reveals [Research Study] – Keeper Blog. Retrieved April 13, 2017, from https://blog.keepersecurity.com/2017/01/13/most-common-passwords-of-2016-research-study/
Jensen, B. (2013). 5 Myths of Password Security. Retrieved April 13, 2017, from https://stormpath.com/blog/5-myths-password-security
Trustwave.com. (2012). 2012 Trustwave Global Security Report. Retrieved July 11, 2012, from https://www.trustwave.com/Resources/Library/Documents/2012-Trustwave-Global-Security-Report/
Turan, M. S., Barker, E., Burr, W., Chen, L., Locke, G., & Gallagher, P. D. (2010). Recommendation for password-based key derivation: part 1: storage applications. NIST Special Publication, 800–132. http://doi.org/10.6028/NIST.SP.800-132
Zhang, Y., Monrose, F., & Reiter, M. K. (2010). The Security of Modern Password Expiration: An Algorithmic Framework and Empirical Analysis. http://doi.org/10.1145/1866307.1866328
Images Used
Main Graphic retrieved from http://now.avg.com/25-passwords-you-should-avoid/
Figure 1: 25 most common passwords of 2016 retrieved from https://blog.keepersecurity.com/2017/01/13/most-common-passwords-of-2016-research-study/
Figure 2: Aircrack-ng retrieved whilst performing labs – TomBrett.ie