Certain Ransomware Victims may be able to decrypt files without paying ransomware
It looks like one of the latest strains of ransomware may be flawed.
Securelist.com explain the some facts about the Torlocker ransomware as follows “Our analysis has shown that Trojan-Ransom.Win32.Scraper was presumably written in assembler, which is unusual for this type of malware. The Trojan uses the Tor network to contact its “owners” – something that is apparently becoming a norm for the new generation of ransomware – and the proxy server polipo. This piece of malware often lands on users’ computers via the Andromeda botnet.
Trojan-Ransom.Win32.Scraper encrypts the victim’s documents and demands a ransom ($300 or greater) to decrypt them. If the malware gets deleted by a security product after the files are encrypted, the Trojan installs bright red wallpaper on the Desktop, containing a link to its executable file. Thus, users have a chance to re-install the Trojan and report to its owners that they have paid the ransom: to do so, users need to enter payment details in a dedicated TorLocker window. This data will be sent to the C&C server which will either reply with a private RSA key or notify that there was no payment.”
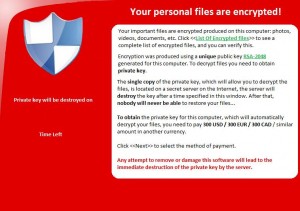
A Screenshot from the Ransomware encryptor is shown below
In general they say that although the ransomware encrypts all files with 256 bit encryption, that in most cases (over 70% tested) that they can be decrypted due to errors made in the cryptography algorithms!
To decrypt the files, Kaspersky have developed a application called the ScraperDecryptor utility which can be downloaded from http://support.kaspersky.com/viruses/disinfection/11718
References
1. securelist.com A flawed ransomware encryptor Victor Alyushin, Fedor Sinitsyn 8 April 2015
https://securelist.com/blog/research/69481/a-flawed-ransomware-encryptor/ Retrieved 13 April 2015
2. support.kaspersky.com Safety 101: Virus-fighting utilities 15 Jan 2015
http://support.kaspersky.com/viruses/disinfection/11718 Retrieved 13 April 2015